THM Basic Malware RE
Task 2 - Strings::Challenge 1
After downloading the provided executable, we need to find a certain flag which a md5 hash of it gets generated.
We firstly try viewing the executable using strings strings1.exe_.
!This program cannot be run in DOS mode.
Rich
.text
`.rdata
@.data
.CRT
@.rsrc
@.reloc
QZ^&
QXRhl
TAhR
j0hT
FLAG{THE-DEPICTED-THE-IMPORTANT-THE}
FLAG{INCLUDES-COLLECTIVE-AND-SOCIALIST-INQUIRY}
FLAG{LAW-IDEOLOGICAL-INTO-THE-THE}
FLAG{COMPETENCE-ISSUE-PERSONAL-THE-LAW}
FLAG{MATTERS-POLITICAL-DETERMINATION-ITS-SOCIALIST}
FLAG{BODIES-PROMOTE-NATIONWIDE-COLLECTIVE-SOVIET}
...
However, as we can see, there is a plenty of flags available, and finding it would be a hassle.
Using x64dbg, we can go to the EntryPoint of the executable, and then find the executable that gets hashed.
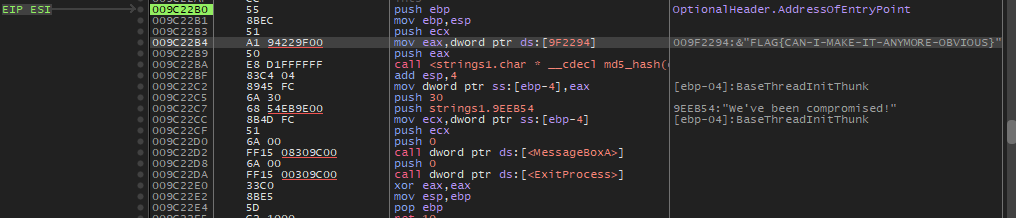
Question
What is the flag of which that MD5 gets generated?
Answer: FLAG{CAN-I-MAKE-IT-ANYMORE-OBVIOUS}
Task 3 - Strings :: Challenge 2
Here, we directly putting our executable in x64dbg. When we reach the entrypoint of our executable, we can directly see each character of the flag that is being pushed into ebp.
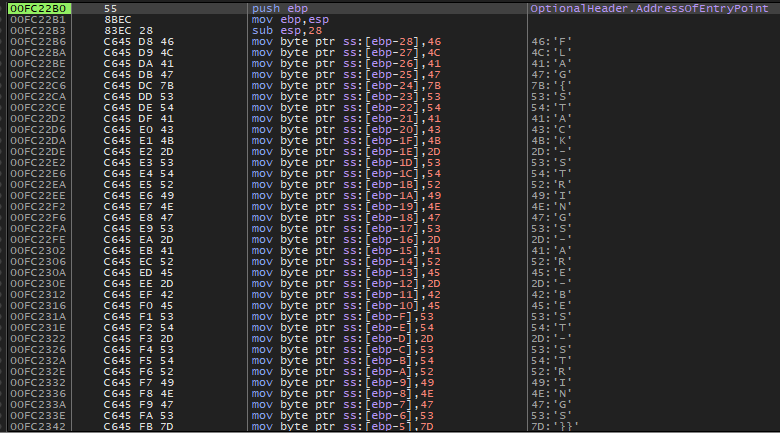
Question
What is the flag of which that MD5 gets generated?
Answer: FLAG{STACK-STRINGS-ARE-BEST-STRINGS}
Task 4 - Strings :: Challenge 3
In this case, the problem is a bit more complex so we will use ghidra instead of x64dbg.
When we look into our program, we can see this:
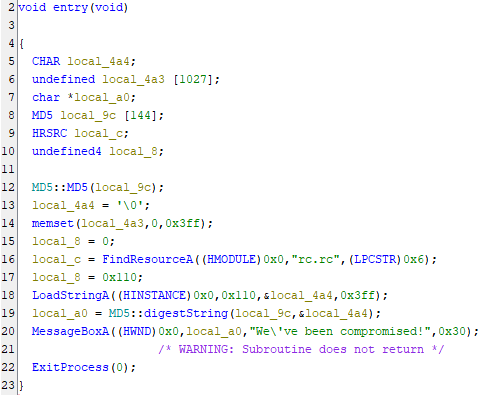
We can see that we have FindRessourceA and LoadStringA.
int LoadStringA(
[in, optional] HINSTANCE hInstance,
[in] UINT uID,
[out] LPSTR lpBuffer,
[in] int cchBufferMax
);
HRSRC FindResourceA(
[in, optional] HMODULE hModule,
[in] LPCSTR lpName,
[in] LPCSTR lpType
);
-
FindResourceA: Searches for a resource in a Windows executable file. Here it searches in this program for “rc.rc” but it doesn’t seem to have a partucal purpose. -
LoadStringA: Loads a string resource from a Windows executable file into memory. Here, it searches for a string with id 0x110 (272 in decimal) and returns the pointer address of where it has been copied.
Now, our goal is to find a string associated with this ID in the .rsrc string stable.
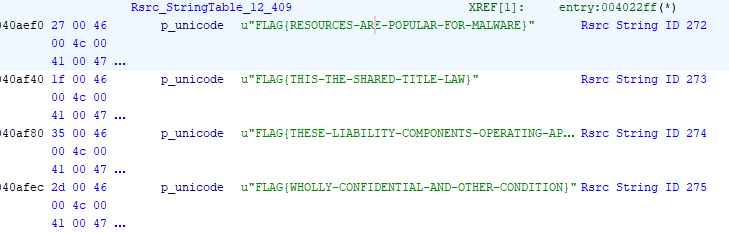
Question
What is the flag of which that MD5 gets generated?
Answer: FLAG{RESOURCES-ARE-POPULAR-FOR-MALWARE}
Enjoy Reading This Article?
Here are some more articles you might like to read next: